.jpg?width=456&height=456&name=cerberus_20(1).jpg)
Many organizations assume that strong cybersecurity equals complete protection. While cybersecurity is essential, it’s only part of the equation. Threats are evolving faster than defenses can keep up, making it nearly impossible to block every attack.
Cyber resiliency completes the equation by focusing on how businesses respond and recover when defenses fail. It emphasizes continuity, keeping systems running, reducing downtime, and restoring operations quickly.
In this post, we’ll break down the difference between cybersecurity and cyber resiliency, explain why both matter, and show how to build a strategy that protects your business from every angle.
Defining Cybersecurity: Your First Line of Defense
Cybersecurity refers to the tools, technologies, and processes that protect your systems, networks, and data from unauthorized access and cyberattacks. It’s your organization’s first line of defense against threats like malware, ransomware, phishing, and data breaches.
The primary goal of cybersecurity is to create barriers that stop threats before they can cause damage. This includes protecting sensitive data, maintaining system integrity, and ensuring that only authorized users can access critical resources.
Core Cybersecurity Components
A strong cybersecurity strategy typically includes:
- Threat Detection and Network Security: Monitoring tools, firewalls, and intrusion detection systems that identify suspicious activity and block threats before they reach your network.
- Access Controls: Measures like multi-factor authentication and role-based permissions that limit access to sensitive data.
- Employee Training: Ongoing education that helps staff spot phishing attempts, social engineering, and other common risks.
- System Hardening: Regular updates, patches, and configuration reviews that close security gaps and reduce vulnerabilities.
What Is Cyber Resiliency? A Strategy for the Inevitable
Cyber resiliency takes a different approach. It recognizes that some threats will get through, and prepares your organization to respond quickly, recover effectively, and keep operations running. The goal isn’t just to avoid incidents, but to be ready when they happen.
Key Components of Cyber Resiliency
- Incident Response Planning: Documented procedures that outline what to do when a security event occurs, including who to contact, how to contain the threat, and how to coordinate response efforts across teams.
- Backup and Disaster Recovery: Reliable backup systems and recovery processes that allow you to restore data and systems quickly after an attack, outage, or failure.
- Business Continuity Planning: Strategies that help maintain essential operations during a crisis, including alternative workflows, tools, and communication methods.
- System Redundancy: Secondary systems and built-in failover capabilities that keep key services running when primary systems go offline.
- Crisis Communication: Pre-planned communication protocols to keep employees, customers, and stakeholders informed throughout the incident and recovery process.
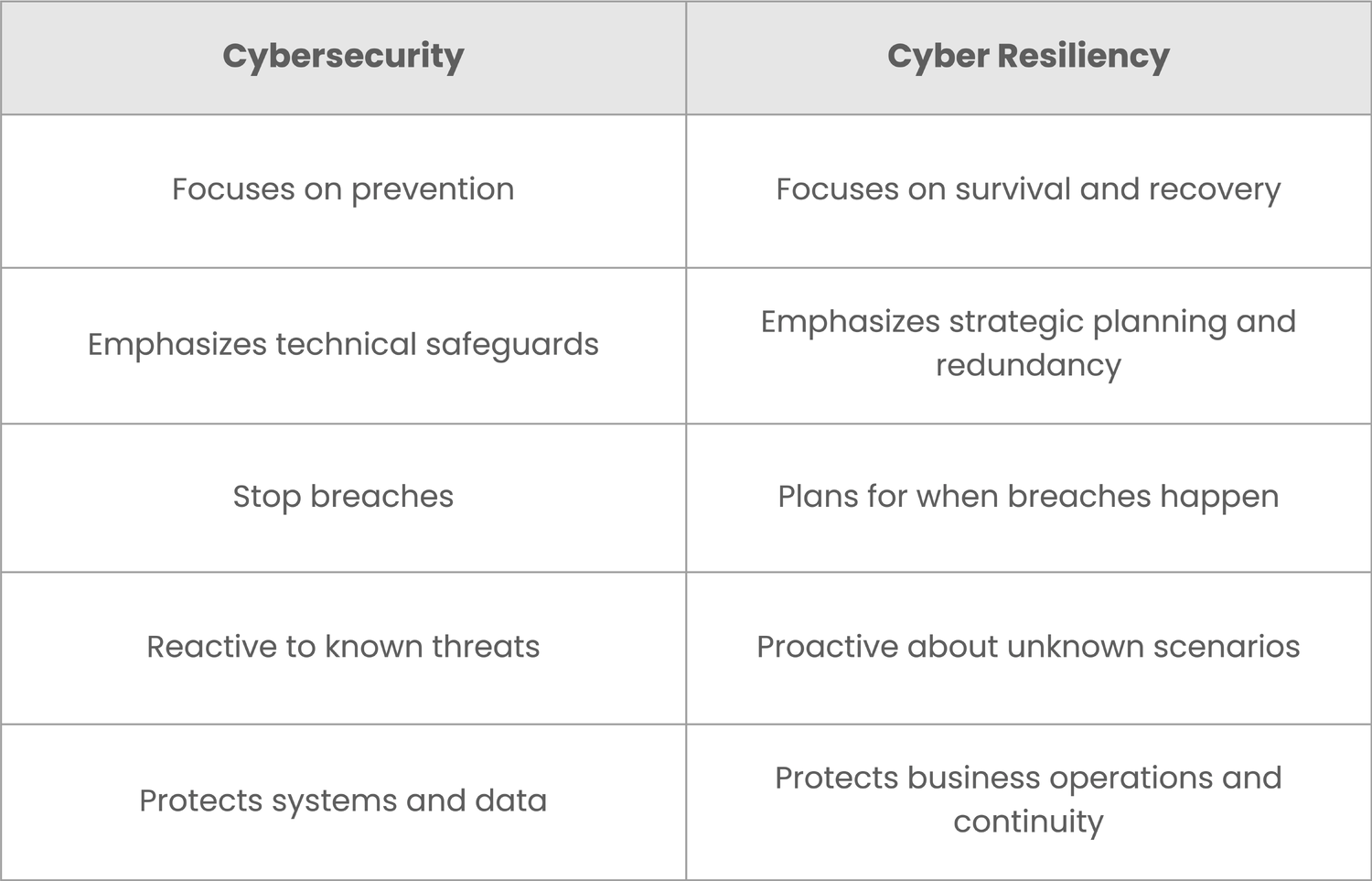
Cybersecurity vs. Cyber Resiliency: Key Differences
Understanding the distinction between these two approaches is crucial for building effective protection:
![EPI - cybersecurity Table-1-2]()
Why Both Matter, Especially for SMBs and Mid-Market Companies
Cybersecurity helps you avoid attacks. Resiliency helps you survive them.
For small and mid-sized businesses, both are essential. Threats like ransomware, phishing, and supply chain vulnerabilities are becoming more advanced, and no organization is too small to be targeted.
Many businesses invest heavily in cybersecurity tools but stop there. Without a plan for how to respond and recover, a single breach can lead to extended downtime, permanent data loss, or serious compliance issues. The result is not just an IT problem. It’s a business disruption.
Combining prevention with preparation gives you the best chance of staying protected, staying operational, and staying in control when it matters most.
What a Balanced Approach Looks Like
Effective cyber protection requires both preventive measures and resiliency planning. Here's how to build a comprehensive strategy:
Prevention-Focused Measures
Regular Vulnerability Assessments: Conduct quarterly evaluations of your systems to identify and address security gaps before they can be exploited.
Employee Security Training: Implement ongoing training programs that help staff recognize phishing attempts, social engineering tactics, and other common attacks.
Access Controls and Authentication: Deploy multi-factor authentication, role-based access controls, and regular access reviews to ensure only authorized users can reach sensitive systems.
Network Security: Maintain updated firewalls, intrusion detection systems, and network monitoring tools that can identify and block suspicious activity.
Resiliency-Focused Measures
Comprehensive Backup Strategy: Implement automated, regular backups of all critical data and systems, stored in multiple locations including offline or air-gapped storage.
Incident Response Planning: Develop detailed procedures for responding to different types of cyber incidents, including clear roles and responsibilities for team members.
Business Continuity Planning: Create strategies for maintaining essential operations during system outages or other disruptions.
Regular Testing and Drills: Conduct periodic tests of your backup systems, incident response procedures, and business continuity plans to ensure they work when needed.
Cyber Insurance: Consider cyber liability insurance as a final layer of protection to help cover costs associated with successful attacks.
How EpiOn Helps You Build a Cyber-Smart and Resilient Business
At EpiOn, cybersecurity isn’t just about blocking threats. It’s about building a strategy that protects your business today and keeps you prepared for whatever comes next.
We combine proactive protection with long-term planning to help you stay ahead of evolving risks. Our services include:
- 24/7 monitoring and threat detection to catch issues early and respond quickly
- Secure cloud environments that protect your data while supporting remote work and scalability
- Business continuity and disaster recovery planning to ensure your operations can continue during unexpected events
- Customized security frameworks that grow and adapt alongside your business goals
Whether you're starting from scratch or strengthening an existing plan, EpiOn helps you build a foundation for both security and resiliency, so your business can move forward with confidence.
Ready to evaluate your organization's current security posture and resiliency planning? Contact EpiOn today to schedule a comprehensive risk assessment and discover how we can help you build a more secure and resilient business.